An independent security researcher who goes by the name of ‘MalwareTech’ has claimed that he found a way to abuse the ZeroAccess malware’s botnet to initiate reflection DDoS attacks.
 According to the researcher, the severity of any DDoS attack executed using this method could be worse than the typical DDoS attack as it has an above-average amplification factor.
According to the researcher, the severity of any DDoS attack executed using this method could be worse than the typical DDoS attack as it has an above-average amplification factor.
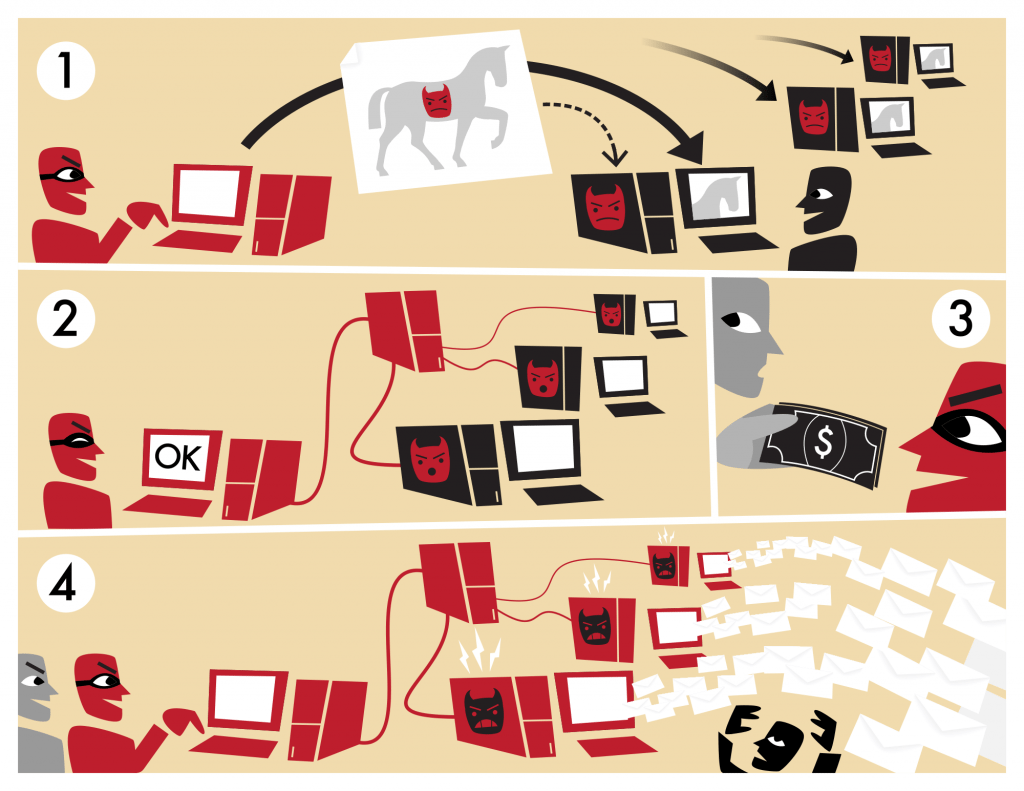
ZeroAccess is basically a trojan program that infiltrates into a Windows system and then sets up its own communication channel with the command and control. This in turn, tells the program to download a host of other (more threatening) malware – most typically bitcoin mining software or click fraud bots that secretly operate without the user even realizing something is wrong.
First discovered in 2011, the ZeroAccess botnet survived a rather extensive takedown attempt by Microsoft in late December. The virtual immunity it boasts is a byproduct of its inherent P2P like structure as well as a highly efficient rootkit component.
Meanwhile, MalwareTech also discovered that the botnet allowed its bots to communicate with other bots in a complicated and hard-to-be-detect environment. Some of these bots act as supernodes or smaller servers while the rest would contribute it as just end-bots.
ZeroAccess uses UDP packets to communicate from the command and control server to its supernodes and workers (end-bots).
Every time a UDP packet reaches a supernode, the bot automatically adds more information to the packet so it is more knowledgeable with regard to the network’s structure. The supernode normally adds 408 bytes atop the original 16, making a total of 242 bytes.
