911 is the emergency response phone system used in the US. A new report claims that the famous system is vulnerable to DDoS cyber attacks. Such attack can disrupt the 911 network across the nation. Researchers claim to have found a way to disable the service across an entire state for an extended period.

According to a Researchers at Israel’s Ben-Gurion University, there is a way to disable the emergency system across an entire state for an extended period using a telephony denial-of-service (TDoS) attack. This attack targets 911 call centres. The 911 system relies on routing and connecting 911 calls to nearby public call centres, known as public safety answering points (PSAP). Researchers claim that it is possible for a hacker to cause mobile phones to call 911 automatically without a user’s knowledge, which would end up clogging up the PSAP’s queues. This could stop legitimate callers from reaching the service.
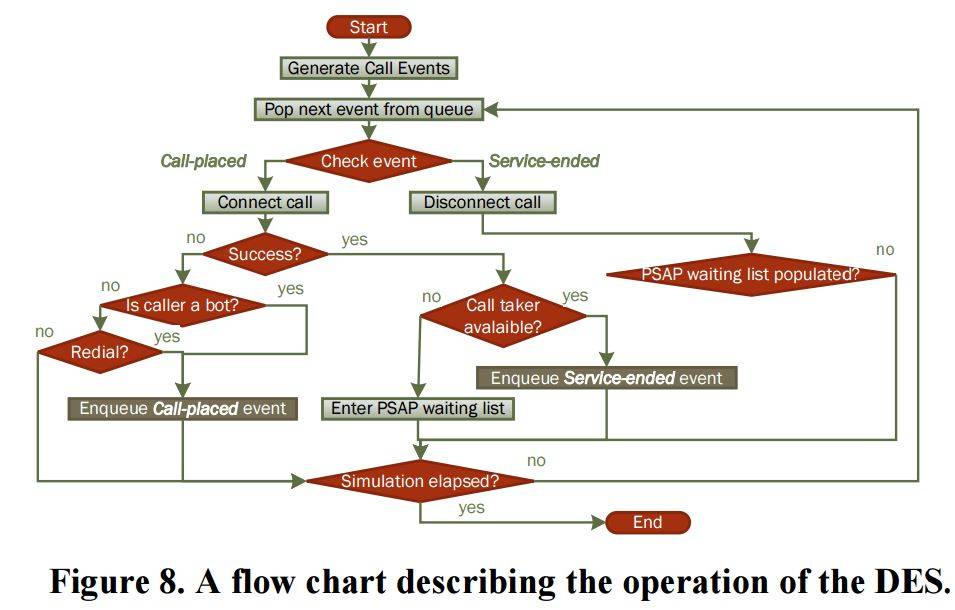
About 70% of the approximately 240 million calls placed to 911 call centres are made from mobile phones. As per Federal Communications Commission (FCC) regulations, wireless carriers must forward all 911 calls to a PSAP, regardless of caller validation. A malicious hacker can exploit this rule to cause disruption. A hacker can mask and randomise a mobile phone’s identifiers, by placing a rootkit within the baseband firmware of a mobile phone. This creates a cell phone with no identity.
Researchers Mordechai Guri, Yisroel Mirsky, and Yuval Elovici wrote in the report that was passed to the Department of Homeland Security before being released to the public:
“Such anonymised phones can issue repeated emergency calls that cannot be blocked by the network or the emergency call centres, technically or legally. We found that with less than 6K bots (or $100K hardware), attackers can block emergency services in an entire state (e.g., North Carolina) for days. In this scenario, a caller would wait an additional 45sec-3min and call an average of three times to get emergency service.”
Researchers claim that just 200,000 infected phones distributed across the US would be enough to disrupt 911 services across the country. One killer trojanised app or $100k of hardware is enough.
“This means that an attacker only needs to infect ~0.0006% of the country’s population in order to successfully DDoS emergency services. Under these circumstances, an attacker can cause 33% of the nations’ legitimate callers to give up in reaching 911.
This call volume could disrupt the telephone network itself, preventing legitimate 911 calls from reaching a PSAP – a dangerous situation that was “evident during the 9/11 terror attack which, in effect, caused the population to generate a DDoS attack on New York City’s telephony network by collectively dialing 911”.
Among possible solutions, a mandatory call firewall could be used to identify and block DDoS activities, such as frequent 911 calls. PSAPs implement can also start using ‘Priority Queues’ to prioritise callers with more reliable identifiers when connecting someone to a call-taker.
The problem is PSAPs have no built-in way of blacklisting callers. In case of a large attack, they would have to answer each and every call. Even with a blacklisting system in place, the owner of a hacked device would be blocked from receiving emergency services, even in a time of need.
