Osama Almanna, a security researcher discovered a domain validation flaw in the StartSSL certificate authority (CA), allowing anyone to receive SSL certificates for any domain irrespective of the ownership.
For starters, StartSSL is a web service which enables webmasters to request valid SSL certificates for their domains, recognized in all the major browsers. It is owned by Israeli-based StartCom.

To ensure zero abuse, the service forces each user through a validation process to verify the actual owner of the domain, hence preventing hackers from asking for certificates for sites they don’t own.
Verification could be carried out in a number of ways, out of which the most common practice employed by the vast majority of CAs is to have the user place a certain file on the domain’s server root.
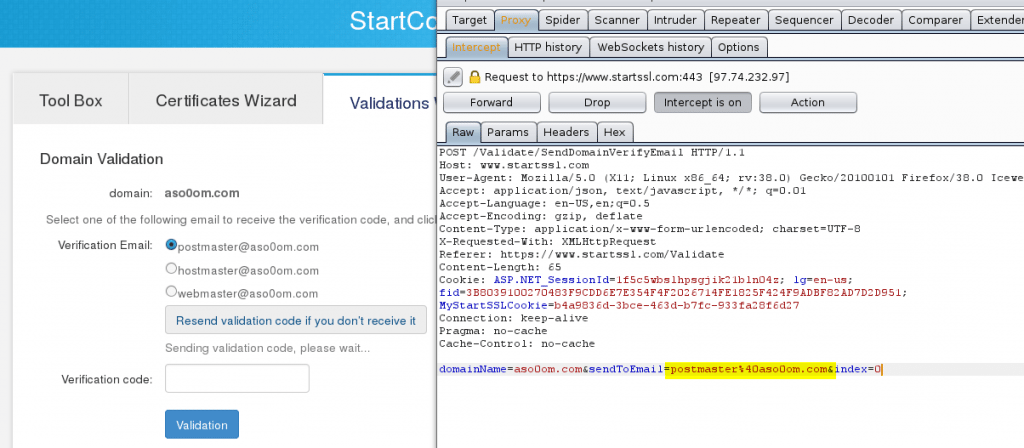
But, the flaw was discovered in email-based user verification, which is employed by StartSSL. In this process, an email with validation code is sent out to users main domain and the email id used are: postmaster@domain.com, hostmaster@domain.com, and webmaster@domain.com
The researcher Osama noted that (via) in the Web form where the user decides to which of these addresses to send the validation code, a skilled attacker could capture the HTTP request sent to the server and modify the included parameters.
And Email address being one of those parameters, a hacker can easily replace it with his own address. This essentially means that anyone could request SSL certificate for google.com or any other website, and have the validation code sent to their own personal inbox.
This loophole could be abused big time by crooks for issuing SSL certificates for banking portals and then use them in their phishing campaigns.
StartSSL was notified by Almanna on the issue and the same was resolved on that day only. It’s good to learn that serious damage was prevented in time.
