G DATA, a German security firm has noticed a new kind of lock-ransomware (a.k.a lockers) that uses a DOS-level lock screen to prevent users from accessing their files. Such ransomwares were prevalent before crypto-ransomware came on the radar. Rather than encrypting the user’s data, this ransomware completely shuts off the user from accessing it.
Most of such cases involved desktop-level lock screen, with the exception of ransomware families that only locked up the browser’s window (called browser lockers, or browser ransomware).
These ransomware threats are easily removable, hence, the hackers moved on to crypto-ransomware variants which are more efficient in convincing infected victims to pay.
Therefore, it’s strange to notice a lock-ransomware these days, though there are pretty relevant in mobile devices.
The name of the latest lock-ransomware discovered by G DATA researchers is Petya. It is aimed at human resource departments and spread via spear-phishing campaigns. HR employees are sent emails with links to a dropbox file in the name of applicants. It’s an executable .exe file named portfolio-packed.exe, which when executed, locks down the PC with a blue screen. The malware also alters the hard drive’s MBR, preventing the OS from starting and hijacking the boot process into a malicious routine.
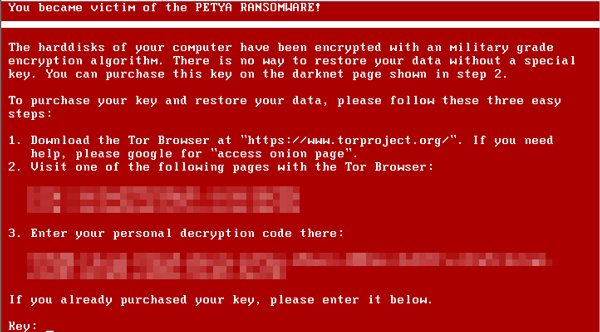
Later when the user restarts the PC, the computer enters a fake CHKDSK(check disk) process that, after it finishes, loads Petya’s lock screen, at the computer’s DOS level. There is no way out of it.
On the very screen, a link to the ransomware’s payment site, hosted on Tor is displayed. At the mentioned site, the user can buy a decryption key that can be entered at the bottom of the DOS lock screen. The crooks behind Petya claims file encryption too, but it can’t be verified as of now.
The researcher team is yet to find a workaround this lock-screen and booting the OS.
Other than G DATA, Cyphort and Trend Micro have confirmed the presence of Petya ransomware threat. Below is a video of Petya in action.
UPDATE: The DropBox team contacted us on the issue, and reported needful steps have been taken to ensure zero tolerance on user’s data. Following is what Dropbox team had to say.
We take any indication of abuse of the Dropbox platform very seriously and have a dedicated team that works around the clock to monitor and prevent misuse of Dropbox. Although this attack didn’t involve any compromise of Dropbox security, we have investigated and have put procedures in place to proactively shut down rogue activity like this as soon as it happens.
