There are more and more phishing scams every day, but the newest Gmail scam is pretty dangerous and hard to notice. The scam managed to fool many users and even some security experts. Like many other online scams, this one can gather private data, scour through your emails, and use your email address to send the phishing email to other users.
Mark Maunder, CEO of Wordfence – a WordPress security service – detailed the scam on the Wordfence blog. According to Maunder, “The way the attack works is that an attacker will send an email to your Gmail account. That email may come from someone you know who has had their account hacked using this technique. It may also include something that looks like an image of an attachment you recognize from the sender.” The email contains a couple of image attachments that are disguised as a PDF file.
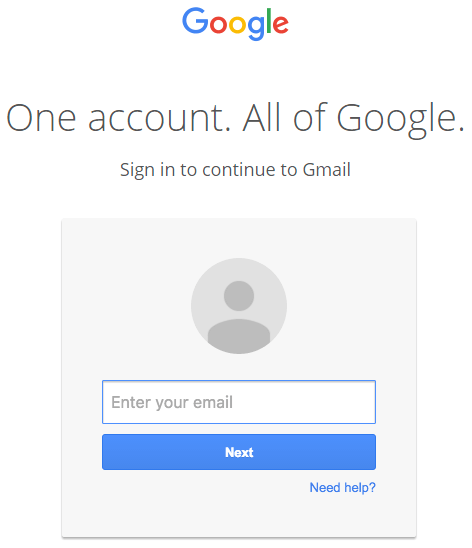
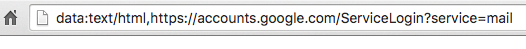
The scam is so effective because it shows a regular Gmail login page along with “accounts.google.com.” address in the location bar, making users believe the login page is genuine. But, there are some differences. For instance, in front of the host name, there’s an attached “data:text/html” data file. If you receive an email that leads you to a login page with the “data:text/html” in the address, do not provide your login credentials. Make sure that there’s nothing in front of the host file name and verify that the protocol and the host name don’t look like on the picture below. The hacking method used is known as URI or data uniform resource identifier.
A person who faced the scam shared that “The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list.”
Aside from verifying that there is no “data:text/html” in the address bar, you should enable Google’s two-step verification for Gmail, because the attackers would need the One Time Password (OTP) to login to your account if using Gmail two-step verification.
