A very shocking report from Arstechnica says that a large number of Mac apps including uTorrent and Camtasia are vulnerable to hijacking, man-in-the-middle attacks. Such attacks are meant for installing malicious code in the app, and eventually, on the system. The vulnerability exists in a 3rd party software framework called Sparkle that is used by apps to receive updates.
Apps fall prey to this vulnerability when they use an exploitable version of Sparkle coupled with an unencrypted HTTP channel for receiving data from the update servers. Radek, a security engineer, has stated that the attack is possible on Yosemite as well as the latest El Capitan Mac platform.
The number of apps that have been affected by this vulnerability is not yet known, as the exploit is not easy to find. Radek says that the number of affected apps is “huge” and includes DuetDisplay v1.5.2.4, uTorrent v1.8.7, Sketch v3.5.1, and Camtasia 2 v2.10.4. It is being said that DXO Optics Pro and Hopper reverse engineering tool are also vulnerable.
According to Radek, another lesser severe Sparkle vulnerability could be exploited against update servers that are poorly configured, and attackers could replace the update files with malicious ones. Radek said in a mail to Arstechnica:
The problem is that developers who created their applications need to update Sparkle framework inside their apps, which is not trivial.
This process requires [a developer] to:
– Download the newest version of Sparkle Updater
– Check if new version of Sparkle is compatible with the app
– Create some test cases, verify update and so on
– Address this vulnerability and publish new version of the appNow, this is the moment when people can check for the update and replace this particular app version on their computers with the newest one.
It all depends on the complexity of an application, its size and maintainers. That’s the reason why some developers don’t want to update or can’t update Sparkle in their applications.
If you use Mac, there is no way to know which apps are affected by this vulnerability and which are not. Make sure that you avoid unsecured Wi-Fi networks or using a virtual private network when downloading apps.
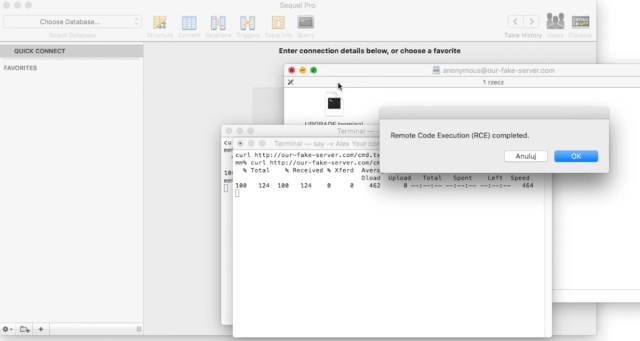
Below is a video that shows how a vulnerable version of Sequel Pro can be exploited:
