Even the Mac is no more immune from the ransomware as the world’s first fully functional ransomware made its made into the Mac system. The ransomware family targeted the Mac users with an infected version of the Transmission BitTorrent client. The hackers were able to hack into the Transmission project’s website and they replaced the original file with the one which contained KeRanger ransomware.
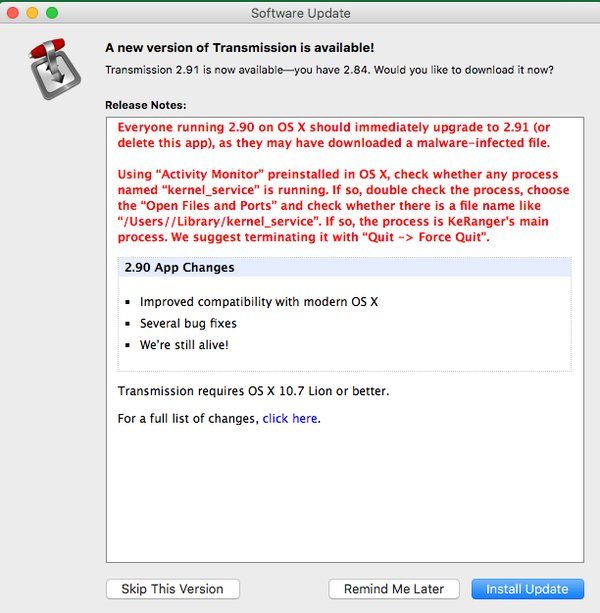
The crooks very clever enough to hide their tracks by activating the encryption process only after three days once the Transmission client got installed. This was first found by the Palo Alto Networks which reported that the Transmission website provided a malicious Transmission client between 11:00 AM PST, March 4 and 7:00 PM PST, March 5, 2016.
Well, this is some silver lining as most of the users would still be able to remove this completely as it wouldn’t have still started the encryption process. If you recently downloaded the Transmission client, follow these easy steps to remove this ransomware:
Step1: Check your drive for the following files
/Applications/Transmission.app/Contents/Resources/General.rtf
or
/Volumes/Transmission/Transmission.app/Contents/Resources/ General.rtf
If you find any of these two in your search results, then you have installed the infected version of the Transmission client and you are advised to delete this version ASAP.
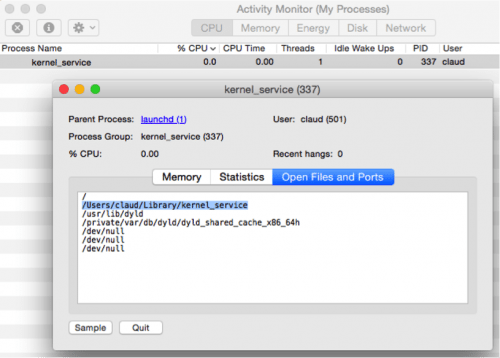
Step 2: Check whether you have a process named ‘kernel_service.’ Running using the OS X Activity Monitor. There may be other apps too which use this process, so we need to make sure by double clicking the process. Double-click and choose the ‘Open Files and Ports’ tab. If you find a file named ‘/Users/Library/kernel_service’, then the KeRanger is running on your system and you should immediately stop this process by selecting ‘Quit -> Force Quit’.
Step 3: We would also recommend to check the ~/Library directory for the following files and do delete them if you find any of these:
.kernel_time, .kernel_complete or kernel_service, kernel_pid
We are sorry to say that the users who already have their files encrypted by the KeRanger are left with no option but to pay the ransomware fee. The ransomware encrypts the file using a very strong algorithm which is still to be cracked. However, Apple has taken necessary steps now by revoking the developer certificate and adding the ransomware’s signature to Mac’s built-in anti-malware toolkit, XProtect. Users trying to run the infected Transmission Mac client v2.90 will now see a warning to abort the operation.
Also check: Best Torrent Sites
Hurry if you have still not got your files encrypted and follow the above-mentioned steps to protect your Mac from this ransomware.
