No doubt Internet is the greatest technological advancement humans have made in their entire history. It has created a whole new world which is global, virtual, mostly non-violent and is mostly neutral. advancements within this virtual world opened up a lot of things like telecommunications, online shopping, e-finance, and a revolution in the form of social networking. But soon, this virtual world fell prey to an equally new form of terrorism. This cyber terrorism isn’t like the conventional terrorism. It employs a number of tools e.g., viruses, malware, hacking, cracking, ransomware etc., to fulfill their objectives. One of the most notorious of these ways comprises of a militia of hackers who aim at stealing your virtual identity or contents from your virtual world. Despite a number of government and community efforts, these hackers have been successful in stealing password and using it to break into users’ virtual world.
Initially, it was advised by experts to use a strong password with a combination of alphanumeric and special characters, to make it hard for hackers to guess. Though hackers developed a number of tools to easily break your seemingly non-guessable and thus impeccable password. So with the strong password technique out of the question, we are faced with the problem of security of passwords. However, some online service providers have shown success with the introduction of two-step verification while logging in.
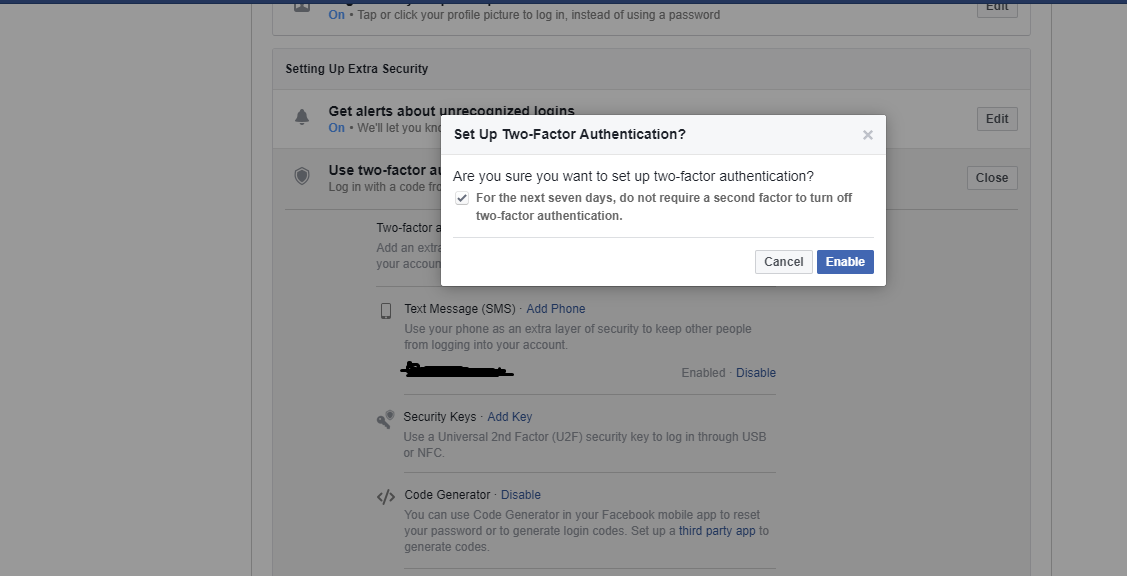
The two-step verification or two-step authentication provides you with added security from malicious logging attempts. It works by sending the original user a text message or other media which contains a unique code. The user will be logged in only after he enters this unique code while logging in. This is done to verify that the person attempting to login is actually the account holder and some random hacker trying to break in.
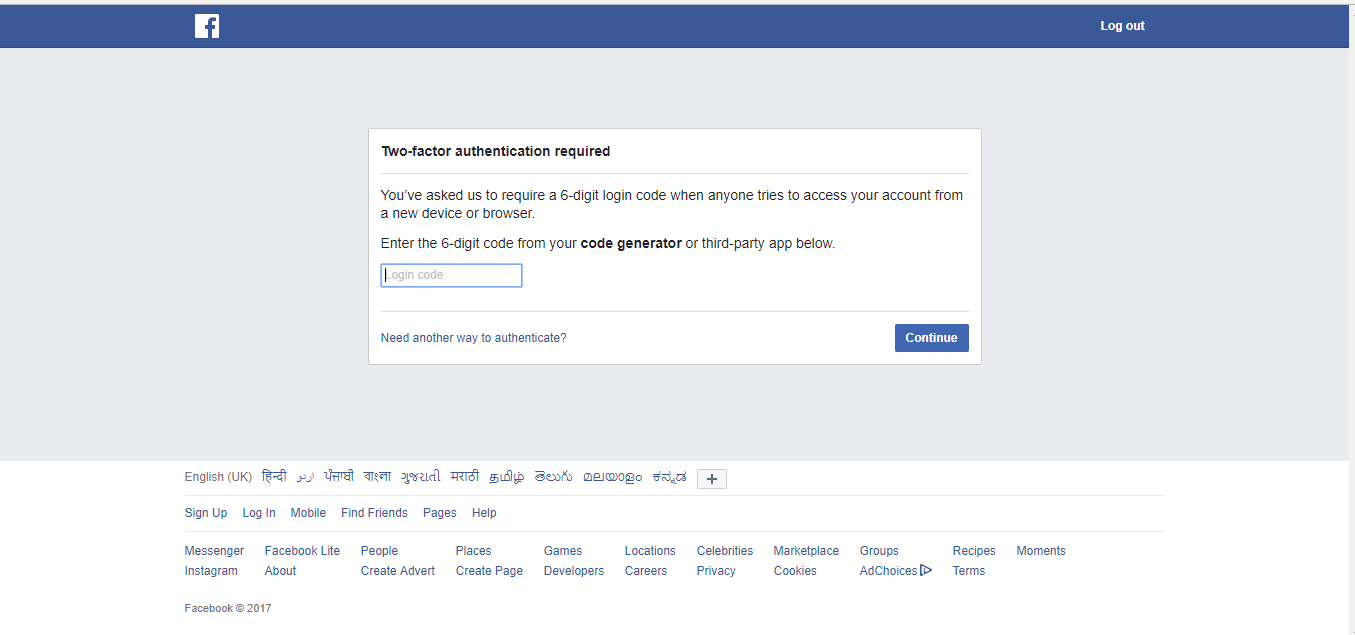
Two-step authentication has been very successful in blocking malicious login attempts by hackers. Each time when you login to your account you are asked a second piece of information besides your id and password. This second piece of information is different every time, which you come to know only after you receive a text in this regard so how come a hacker will know about the new code sent to you every time even when someone else with your password and user id, enters it.
If you haven’t yet signed up for two-step verification, you can very well start with Google. You need to open Settings then locate and open Security. There you will find an option for initiating the two-step authentication. For Facebook, you have to again visit Settings and from there you need to locate Login approvals inside the Security subhead. Apple users will have to visit AppleID instead of settings in iTunes to sign up for two-step verification. When done it is highly advised that you also log out from all other devices for it to work effectively.
It is highly recommended that you initiate this two-step verification for your email account because it’s the most sensitive portion of your cyber identity and a vulnerable email account can always be used to reset the password of every other online service.
In the beginning, you might find it inconvenient to wait for a message and then enter it whenever you are trying to log in. There is also a bypass option for it, you can choose to bypass two-step verification on any computer or device of your choice. However, it is not recommended as someone with access to your computer like your room partner or a jealous sibling might override the two-step authentication and post something embarrassing. Also, you should avoid bypassing two-step verification when you are accessing your account from a public computer or if you are temporarily using someone else’s computer.

Though Two-step verification is really important for your cyber security sometimes you may find it inconvenient to get up and reach for your phone to enter the verification sent to it after you have entered your password. People have already expressed concerns over its utility over unavailability of the cellular network while traveling. However, most of the online service providers like Google, Facebook, etc., run a backup service. Their backup service generates a backup code for when you are offline. Though, it is not possible to carry the backup code all time with you.
Two-step verification is important to fend off malicious login attempts by hackers. However, it is practically impossible to set up a two-step verification for a Twitter Page, or similar blogs. Because it is handled by a number of teams, so it will be of use only if there is a shared phone. However, efforts are being made to overcome this difficulty. If you are still worried about the situation where you lose your phone, then that has been taken care of. Providers like Google, offer to set up a recovery
If you are still worried about the situation where you lose your phone, then that has been taken care of. Providers like Google, offer to set up a recovery address in case the verification code is unable to reach you. Two-step verification security may prove to be inconvenient sometimes but a moment’s inconvenience is far better than losing your account to a hacker or paying him loads of ransom in exchange for getting access to your account. Though, there are reports of introducing biometric authentication to remove the vulnerability associated with the good old password. But it may take a time to actualise.

Two-step verification security may prove to be inconvenient sometimes but a moment’s inconvenience is far better than losing your account to a hacker or paying him loads of ransom in exchange for getting access to your account. Though, there are reports of introducing biometric authentication to remove the vulnerability associated with a good old password. But it may take a while to actualise.
