Versions 1.0.2g and 1.0.1s of the OpenSSL project have been released for fixing some several security vulnerabilities that might otherwise lead to the DROWN attack, a very sever security issue. Classified as CVE-2016-0800, DROWN enables hackers to steal encrypted information by breaking HTTPS. Short for “Decrypting RSA using Obsolete and Weakened eNcryption“, DROWN has been discovered by a 15-researchers team.
DROWN depends on the existence of both TLS and SSLv2 protocols on the machines targeted. Being a cross-protocol attack, DROWN uses the weaknesses of the SSLv2 implementation directly against the TLS protocol. This weakness is a result of the Bleichenbacher attack on the RSA encryption system that is used by TLS as well as SSL. It is being said that the researchers working on the DROWN have come up with new methods of launching Bleichenbacher.
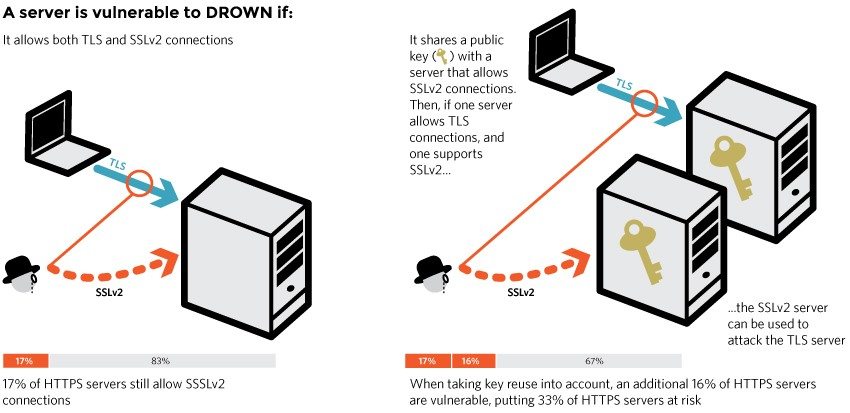
The DROWN attack is meant for TLS, which is considered to be superior than the SSL. Those servers that are still using both TLS and SSLv2 together at the same time are vulnerable to this attack. Also, DROWN can access sysadmins in a very particular server setup that is only using TLS.
Researchers have stated:
You’re just as much at risk if your site’s certificate or key is used anywhere else on a server that does support SSLv2. Common examples include SMTP, IMAP, and POP mail servers, and secondary HTTPS servers used for specific web applications.
Around 33% of all the HTTPS websites in the world are at risk of the DROWN attack. These sites include some of the most popular ones like DailyMotion, Weibo, Yahoo, HostGator, Flickr, StumbleUpon, 4Shared, and much more.
You can find more information on this issue by going to the DROWN Attack website. There’s also a DROWN Vulnerability Checker on the website if you want to check out your HTTPS website’s health.
