Valve-owned digital distribution platform Steam’s security was breached earlier this week by a security researcher who then proceeded onto uploading a fake game on the network in order to draw the company’s attention to its security loopholes.
Apparently, the researcher who goes by the pseudonym ‘rubiimeow’ (Ruby Nealon) wanted to the make the company aware of the fact that their game upload process has serious flaws in it which enabled anybody to release a new title on the Steam Store without requiring to go through the mandatory review process.
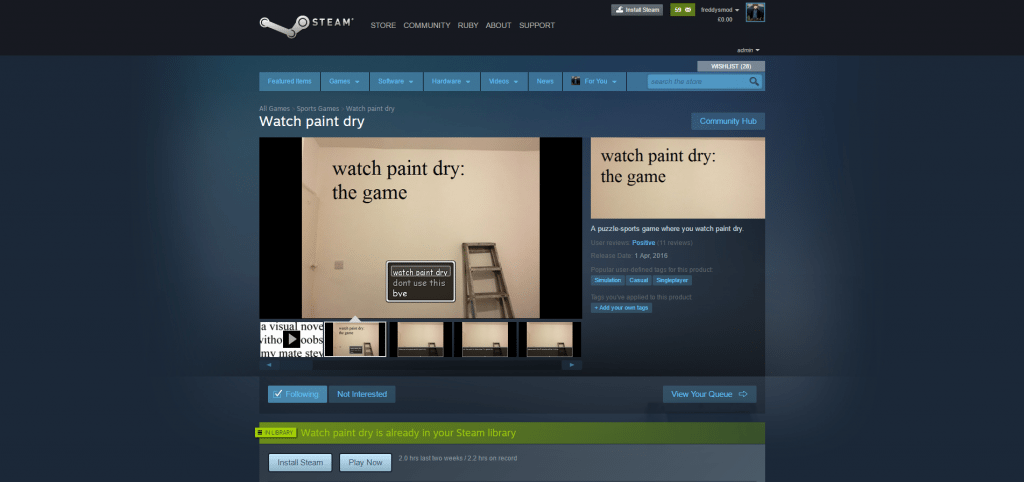
To its credit, Steam was quick to fix the vulnerability soon after. As it turns out, while the vulnerability was relatively easy to exploit, it would require the attacker a Steamworks account (which is only granted to game developers).
Nealon later claimed that he discovered not one, but two flaws in the company’s security infrastructure. The first loophole was actually a part of the Webforms for handling new Steam Trading Card submissions.
He found that with the required know-how, an attacker would be able to exploit a loophole in the form to mess around with the session ID value. Without delving into the technical nitty gritty, this exploit could lead the attacker to the details carried by individual forms.
Once he could lay his hand over the details, the rest was relatively easy. All he needed to do was altering the HTTP request dispatched by the tethered form and then changing the parameters to make appear as if the form had been already reviewed by a Steam employee.
Nealon successfully published a fake game on the platform using this loophole.
