It was during the DEF CON hacker conference that a vulnerability was revealed by some researchers. The flaws are about 20 years old and they could be easily exploited on a specific set of devices. To everyone’s surprise, Microsoft announced that it won’t be fixing the flaw as it can be simply fixed by blocking connections coming from the internet.

The Windows SMB vulnerability was identified by the researchers at RickSense and they called it SMBloris because it is quite similar to the 2009 attack Slowloris. As per the finding, the exploit is a Denial of Service (DoS) and is capable of affecting “every version of SMB protocol and every Windows version dating back to Windows 2000”.
Sean Dillon, senior security researcher at RiskSense was also one of the first researchers to work on EternalBlue, the exploit that lead to the spreading of WananCry ransomware. It was during that analysis that SMBloris was identified. Dillion said that that the issue was privately reported to Microsoft in June itself but Microsoft labelled it as a moderate issue and didn’t pass it on to the security branch to be fixed.
Microsoft’s spokesperson told Threatpost, “The case offers no serious security implications and we do not plan to address it with a security update. For enterprise customers who may be concerned, we recommend they consider blocking access from the internet to SMBv1.”
Windows 10’s market share is growing at a snail’s pace
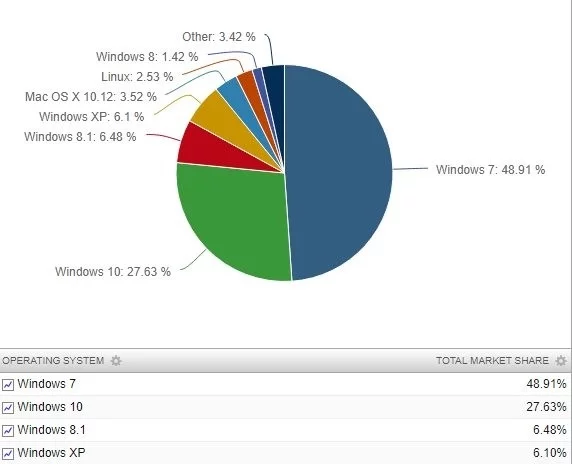
If you didn’t notice, Windows 10 is already two years old and its market share is still almost half of Windows 7 that was first released in 2009. Windows 10 has a market share of 27.63%, while the Windows 7 still stands strong with a share of 48.91%.
The growth of Windows 10 has however grown significantly from 0.02% in June to 0.83%. While that might not sound a great number but the Windows 10 adoption has increased manifold in the last month. This was mainly because of multiple major cyber-attacks including WananCry and Petya.
